Just a few tips regarding the groov family firewall. (Feel free to add your own as time goes by).
-
Since both EPIC and RIO run Linux, you can not open a port lower than 1024.
The reasons for not less than 1024 are steeped history but generally revolve around the fact that when you talk to a service below 1024 you are talking to a secure service and thus you know its an elevated privilege service and the Linux user that runs groov Manage does not have root (superuser privileges) permission.
Now days its more about the certificates that the server or service is using, but in the old days, only root users had access to privileged ports, so you knew who you were talking to.
Bottom line, groov Manage won’t let you open a port less than 1024 and even if you have shell, you probably should not do it either. -
Even if you open a port, that does not mean your program is going to ‘just work’.
What do I mean by that? It means that if you open port 2233 for your Node-RED application, that does not mean it will ‘just work’. You will still need to build a Node-RED flow with the correct nodes to listen and respond to the incoming UDP/TCP traffic on that port.
Remember, you don’t need to open a port to PUSH data out (that’s the whole power of MQTT), you only need to open a port if you have an application connecting to the EPIC/RIO and need to extract data from it. ie, the old poll-response model. -
If you are a shell user and want to double check that groov Manage really has opened the firewall on your nominated port here is an example command and its response ('cause none of us have trust issues right?) that you can use to check.
opto@EPIC-Ben:~$ sudo ufw show raw | grep 22001 0 0 ACCEPT tcp -- eth0 * 0.0.0.0/0 0.0.0.0/0 tcp dpts:22001:22002 /* Opto22 Control Engine */ 0 0 DROP tcp -- eth1 * 0.0.0.0/0 0.0.0.0/0 tcp dpts:22001:22002 /* Opto22 Control Engine */ 0 0 DROP tcp -- wlan0 * 0.0.0.0/0 0.0.0.0/0 tcp dpts:22001:22002 /* Opto22 Control Engine */ 0 0 ACCEPT tcp -- tun0 * 0.0.0.0/0 0.0.0.0/0 tcp dpts:22001:22002 /* Opto22 Control Engine */ 0 0 ACCEPT tcp eth0 * ::/0 ::/0 tcp dpts:22001:22002 /* Opto22 Control Engine */ 0 0 DROP tcp eth1 * ::/0 ::/0 tcp dpts:22001:22002 /* Opto22 Control Engine */ 0 0 DROP tcp wlan0 * ::/0 ::/0 tcp dpts:22001:22002 /* Opto22 Control Engine */ 0 0 ACCEPT tcp tun0 * ::/0 ::/0 tcp dpts:22001:22002 /* Opto22 Control Engine */ opto@EPIC-Ben:
Breaking it down a little. Since you are working with the firewall, you need to be sudo. ufw is the name of the firewall command we are using, in this case uncomplicated firewall (UFW). We are asking to ‘show’ the rules. We want the ‘raw’ output to see the good stuff.
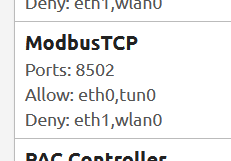
That command alone is going to be a fire-hose and fill the screen with stuff we don’t care about, so we then pipe (|) the output through grep (a filter) and only look for the text ‘22001’ (In this examples case, the PAC Control engine port).
You can see the command output below.
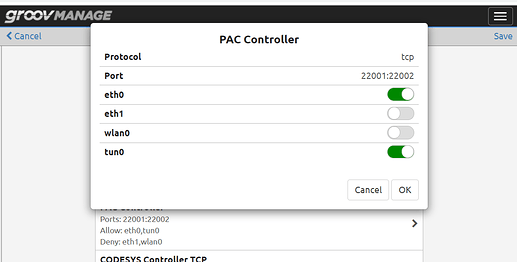
We are ACCEPTing TCP packets on ETH0 and TUN0, and DROPing packets to that port on ETH1 and WLAN0.
Note that its TCP only and if we were using UDP, it would show up as well.
Here is what that rule looks like in groov Manage.
Hopefully those few tips will give you a start to your adventure of getting custom stuff done behind the EPIC or RIO firewall.