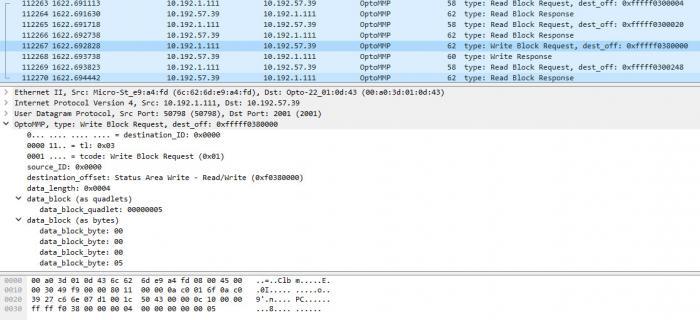
Attention all serious bit-heads who get deep into our [U][B]OptoMMP (memory-map protocol)[/B][/U] – that’s what we use to communicate (either via TCP or UDP) to our PAC brains and controllers. Good news! Wireshark now has a built-in dissector for you.
Note that most PAC Control users rarely, if ever, have to worry about our OptoMMP protocol details. You might notice some addresses when you use PAC Manager, but that’s about it. But if you’ve ever used [U][B]form 1465[/B][/U] and Wireshark (network sniffing tool) to pick apart the individual bits in those packets, this post is for you.
Here’s the good news:
[U][B]Wireshark, as of the 2.0 (stable) release[/B][/U], includes an OptoMMP dissector:
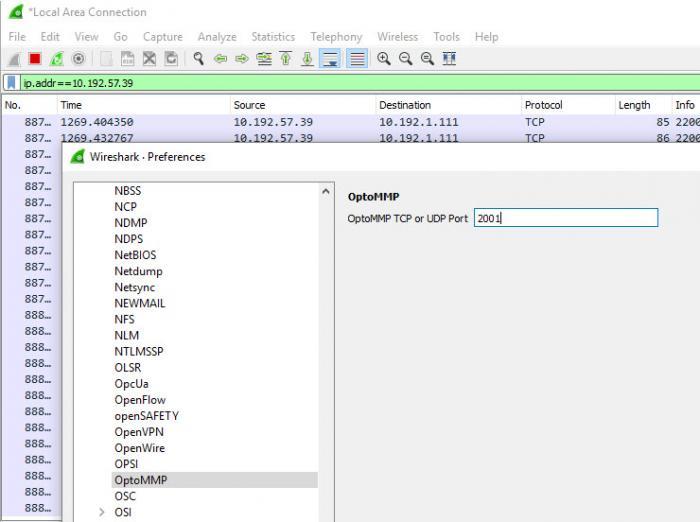
Note, one set-up step: Since TCP port 2001 is already registered to another protocol (dc), you must manually enable the OptoMMP dissector in Wireshark at Edit->Preferences…->Protocols->OptoMMP. Set the Port to 2001 and click OK.
Happy dissecting!
-OptoMary