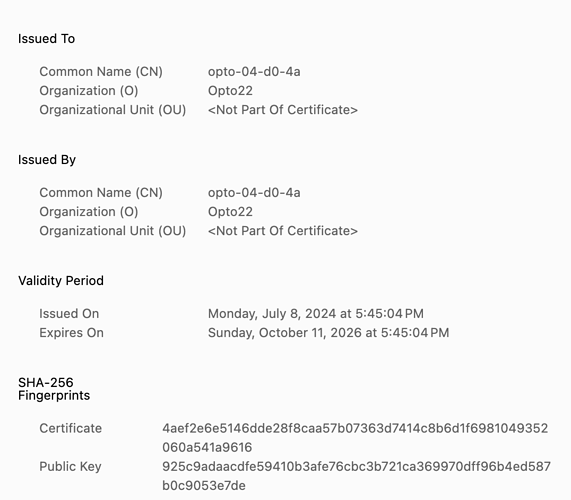
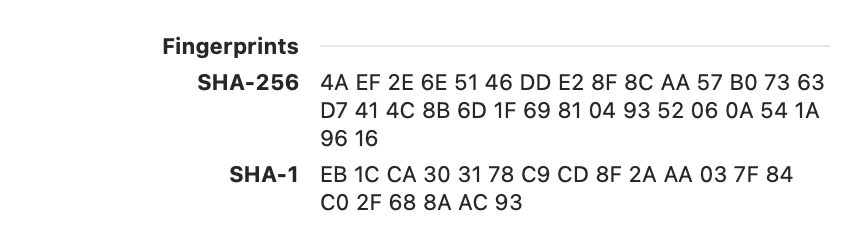
Why does the Web Server Certificate use the older SHA-1 Fingerprint rather than the SHA-2.
Certificates themselves don’t embed fingerprints; they’re something that the software looking at certificates can generate for a quick visual verification. This Information Security Stackexchange answer has a bunch more detail:
As a quick example, looking at the default generated certificate on my EPIC in Chrome shows only a SHA-256 fingerprint:
While looking at the same certificate in Safari shows both SHA-1 and SHA-256 fingerprints:
3 Likes