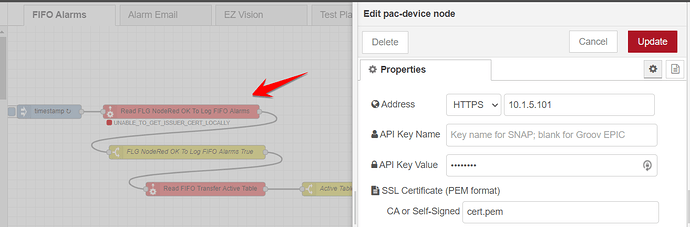
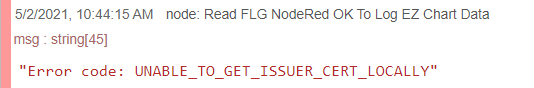
I have a node red flow that uses an HTTP In node to create an endpoint to accept data from other devices. It parses the data and put it into the Epic’s MariaDB.
I am testing it using Postman (https://www.postman.com/).
When I am inside my network I use the local IP address of the Epic (note no port specified). It works.
Here is the post command I use in Postman:
https://10.1.5.101/node-red/test?signalin=7.54&eventdatetime=2021-04-17 13:52:58&unitid=21477&channel=1
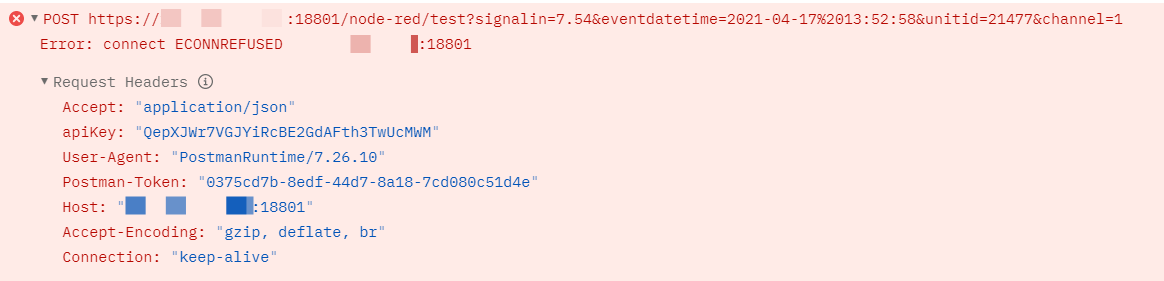
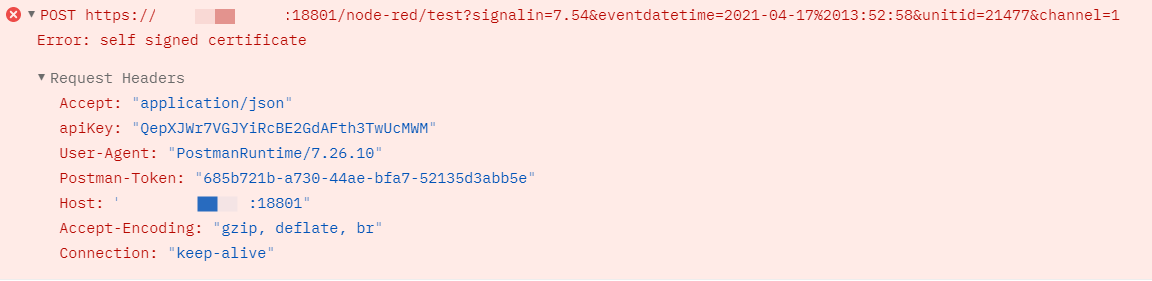
When I am outside my network I am port forwarding all traffic coming to my gateway router xxx.xx.xx.xxx:18801 to the Epic (10.1.5.101). It will not work. I have tried specifying ports 443 and 1880. It will not work.
Here is the post commands I used:
https://xxx.xx.xx.xxx:18801/node-red/test?signalin=7.54&eventdatetime=2021-04-17 13:52:58&unitid=21477&channel=1
I can monitor the router traffic and see that it being allowed through the firewall.
Router log entry when forwarding to port 1880
2021-04-17 16:33:36 Allow xxx.xx.xxx.xxx xxx.xx.xxx.xxx 1880/tcp 56384 18801 0-External 0-LAN Bridge Temp Allowed 52 125 (Node Red HTTP Endpoint 10.1.5.101-00) proc_id=“firewall” rc=“100” msg_id=“3000-0148” dst_ip_nat=“10.1.5.101” dst_port_nat=“1880” tcp_info=“offset 8 S 4253526887 win 64240” geo_src=“USA” geo_dst=“USA”
Router log entry when forwarding to port 443
2021-04-17 16:54:07 Allow xxx.xx.xxx.xxx xxx.xx.xxx.xxx 443/tcp 56919 18801 0-External 0-LAN Bridge Temp Allowed 52 125 (Node Red HTTP Endpoint 10.1.5.101-00) proc_id=“firewall” rc=“100” msg_id=“3000-0148” dst_ip_nat=“10.1.5.101” dst_port_nat=“443” tcp_info=“offset 8 S 2826133454 win 64240” geo_src=“USA” geo_dst=“USA”
Here is the Postman error I get when I try forwarding to port 1880
Here is the Postman error I get when I try forwarding to port 443
What port does the HTTP In node listen on?
Any ideas on how to fix or troubleshoot further?
Thanks,
Craig