If you’ve ever used Node-RED outside of Opto products, on something like a PC or Raspberry Pi, you would have noticed that it does not have any security by default (although it can be added manually – more on this later). On the other hand groov does have built-in security, using both https and requiring a username and password to access anything from groov Manage to the Node-RED editor and even the Node-RED UI dashboard page.
One side effect of this is that anyone with valid credentials to view the dashboard, for example an operator, can also use that username and password to log into the editor – which could contain keys or passwords, and is of course vulnerable to tampering or even being deleted entirely.
Thankfully it is possible to make Node-RED secure on other systems, as described on the Node-RED documentation site here: nodered.org/docs/user-guide/runtime/securing-node-red
We can also make use of this on groov devices providing an additional login layer before users can access the editor, without locking down the dashboard UI(!)
By giving the operators a groov account but not this Node-RED account you can be sure that only the people you want are able to access the Node-RED editor, without also blocking access to the dashboard.
You can basically follow the documentation linked above but to make it simple I’ll break down the steps here.
-
You will need shell access (however a gateway to the internet is not required).
-
Get your password hash and save it. This command will prompt you for the password:
node-red admin hash-pw -
Open the settings.js file with your text editor of choice. You must use
sudo.
sudo nano /usr/share/nxtio/services/node-red/settings.js
or
sudo vim /usr/share/nxtio/services/node-red/settings.js -
Uncomment the adminAuth section under “Securing Node-RED” (lines 108 - 115 from “
adminAuth: {” until the last “},”), delete the default password and replace it with your password hash from step 2. You can also pick any username you want.
adminAuth: {
type: "credentials",
users: [{
username: "admin",
password: "$2a$08$zZWtXTja0fB1pzD4sHCMyOCMYz2Z6dNbM6tl8sJogENOMcxWV9DN.",
permissions: "*"
}]
},
- (Optional) to create additional credential sets for multiple users or have a read-only permission, just add them to the
usersarray like this:
users: [{
username: "admin",
password: "$2a$08$zZWtXTja0fB1pzD4sHCMyOCMYz2Z6dNbM6tl8sJogENOMcxWV9DN.",
permissions: "*"
},
{
username: "user",
password: "$2a$08$zZWtXTja0fB1pzD4sHCMyOCMYz2Z6dNbM6tl8sJogENOMcxWV9DN.",
permissions: "read"
}]
- (Optional) you can also have a default access level (this should be read-only) by adding a
defaultproperty:
adminAuth: {
type: "credentials",
users: [ /* list of users */ ],
default: {
permissions: "read"
}
}
-
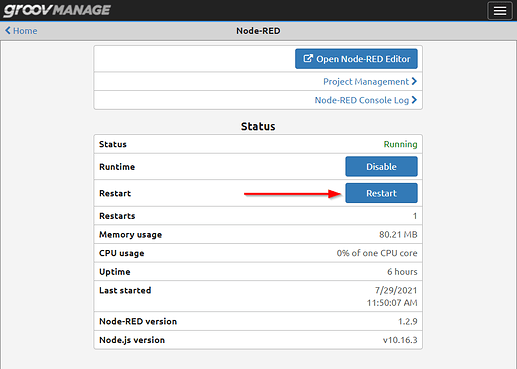
Finally, you will need to restart the Node-RED runtime.
-
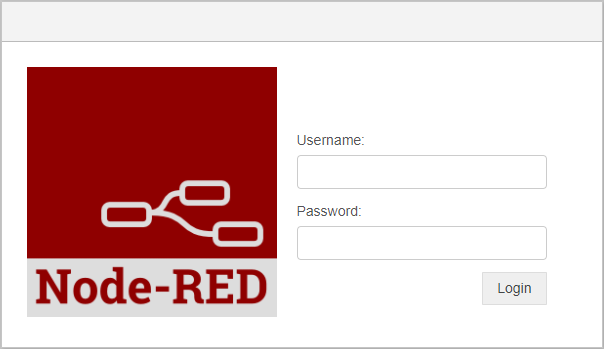
Now when you attempt to open
https://hostname/node-red/you will first have to log in with groov Manage credentials, and then log in again with the Node-RED credentials you just created.
Hopefully this helps keep your Node-RED flows secure without giving up the ability to access the editor when needed.
Happy coding!